Crypto Transaction Security in 2025: How Paymento Secures You

Imagine waking up one morning, eager to check your crypto portfolio, only to find that your funds have vanished and transferred to an untraceable address. Panic sets in as you slowly realise that you’ve fallen victim to crypto hacks and that you may never recover your assets.
What would you do? How will you recover your assets?
With the global cryptocurrency market projected to exceed $2.1 billion and with over 860 million users in 2025, crypto adoption is at an all-time high. However, this growth comes with increased cyber threats, security vulnerabilities, and regulatory scrutiny.
In 2024 alone, over $2.2 billion was lost due to crypto hackers targeting centralized exchanges and DeFi platforms. This highlights the urgent need for increased security measures and crypto compliance protocols.
Whether you’re an individual investor, a merchant accepting crypto payments, or a blockchain developer, understanding the fundamentals of crypto transaction security, compliance, and risks is crucial.
This article will walk you through the essentials of safeguarding digital assets, adhering to regulations, and mitigating risks in the evolving crypto landscape.
How does a Crypto Transaction Work?

A crypto transaction occurs when you send crypto funds from your wallet to another user’s wallet in exchange for value using blockchain technology.
Before approval, the transaction details, such as the wallet addresses, asset amount, and timestamp, are sent to the network of blockchain users. After the transaction is verified through cryptographic protocols, the recipient receives the funds, which are immediately added to the existing blocks of transactions.
For example, a fast-moving consumer goods (FMCG) startup in the United States pays its supplier in China with Bitcoin for the next batch of products to minimize cross-border transaction fees and delays.
Unlike traditional banking, crypto transactions are decentralised, transparent, and irreversible. Therefore, it is important to cross-check all details before clicking on the ‘send’ button.
Components of a Crypto Transaction
“Cryptocurrencies are on their way to becoming the payment method of choice for B2B interactions, signaling a significant shift in business transactions.” Said @cyber_spanish, a crypto enthusiast on Twitter.
Crypto stablecoin transactions moved from $1.9 trillion in February 2024 to $4.1 trillion in February 2025. Crypto transactions are garnering attention. You must familiarise yourself with their core components before initiating one.
Here are the basic ones:
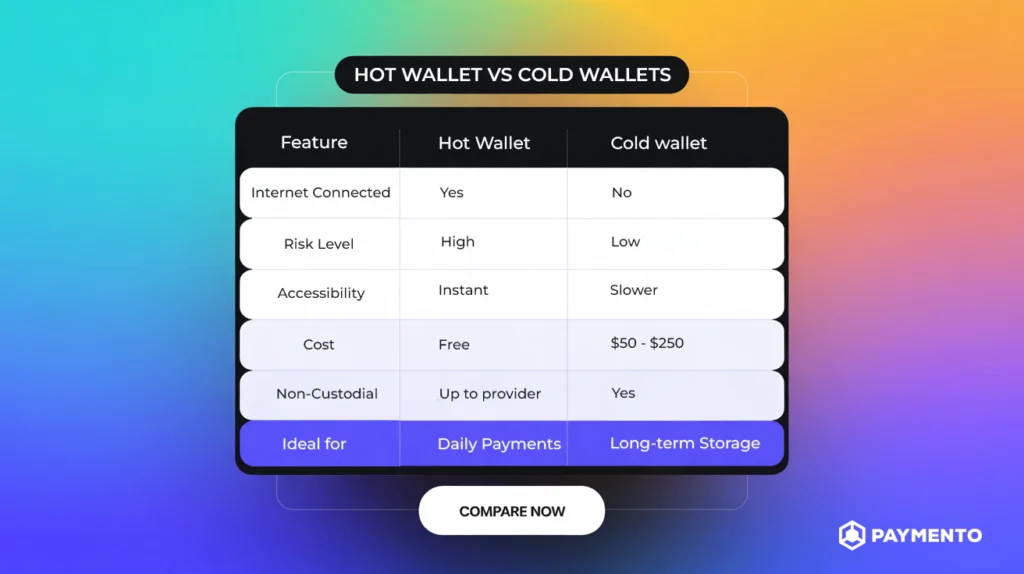
- Wallet: A virtual tool used for storing acquired crypto assets. You can opt for either a cold or hot wallet. Hot wallets are software constantly connected to the internet to make transactions. Cold wallets are hardware devices usually plugged into smart devices to send and receive funds offline.
- Unique Keys: A wallet is assigned private and public keys. Public keys consist of letters and integers used as a wallet address, while private keys consist of letters used to authorise transactions.
- Transaction Fees: Fees charged for the processing of a transaction.
What is Crypto Transaction Security?
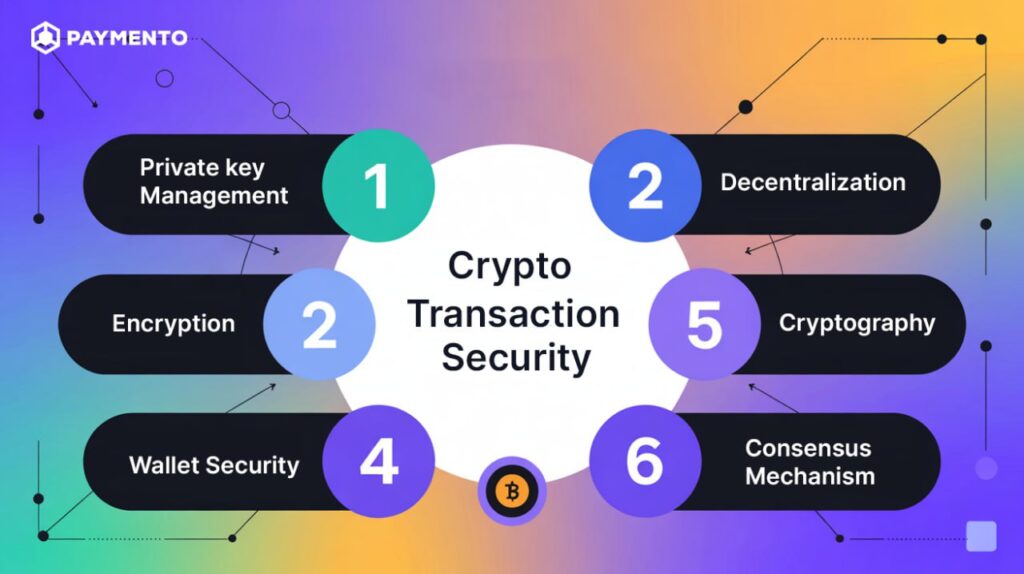
Crypto transaction security refers to the technological and procedural measures to protect blockchain-based transactions from hacks, theft, and authorised access.
These measures include wallet security, payment encryption, and private key management. Blockchain security features such as decentralisation, cryptography, and consensus mechanisms—proof of stake and proof of work—also ensure the safety of digital assets.
In January 2025, Bybit, a crypto exchange platform, lost $1.5 billion worth of Ethereum to North Korean cybercriminals. Furthermore, a total of $1.7 billion was stolen from crypto exchanges in 2023, significantly lower than the $3.8 billion lost to crypto hacks in 2022.
While this shows a decline in cyberattacks due to advanced crypto transaction security measures used by crypto platforms, there are still ongoing vulnerabilities.
What are the Popular Crypto Transaction Security Threats?
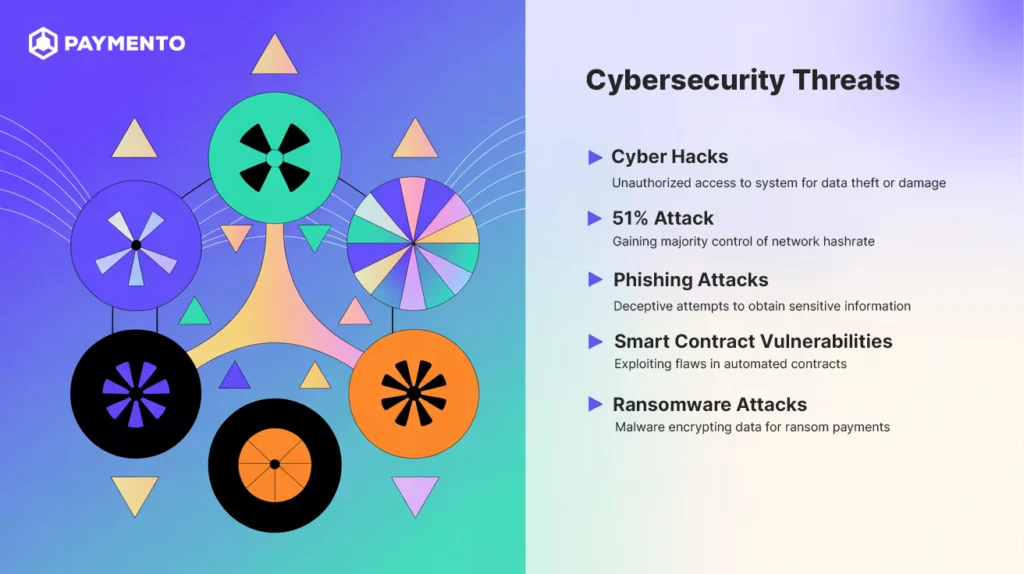
Phishing Attacks
Phishing attacks, a top-leading crypto transaction security threat, are baiting mechanisms cybercriminals use to get users’ sensitive details, such as their private keys and login information.
If you’ve ever come across a fake website or email asking you to input your private credentials, but somehow, you were smarter and blocked them before any actual harm was done, then you’ve encountered and conquered phishing attacks.
In 2022, OpenSea lost $1.7 million to cybercriminals who used counterfeit emails to obtain users’ credentials through a malicious contract. Likewise, in April 2025, cyberattackers pretending to be law enforcement officers stole $1.2 million from UK citizens by collecting their private keys through spoofed fraud reports.
Cyber Hacks
Another prominent blockchain security threat occurs whenever crypto exchanges are hacked due to software and API key vulnerabilities or leaks of sensitive information in the organisation.
Mt Gox, for example, went bankrupt in 2014 after a cyber hack caused it to lose $450 million worth of Bitcoin due to a lack of cold storage for funds. Coincheck, a Japanese crypto exchange, got scammed of $530 million worth of NEM tokens in 2018 for storing crypto assets in a hot wallet.
Smart Contract Vulnerabilities
Smart contracts are self-executing programs built into a blockchain system. They remove the need for an intermediary before transactions are completed. Smart contract vulnerabilities, such as poorly written codes, code bugs, or loopholes, can leave your organization susceptible to malicious attacks.
One of the common ones is the re-entracy attacks where scammers continuously withdraw funds before the smart contract’s loophole is discovered and updated. Coding flaws can also lead to unapproved fund transfers.
A real-life example of this crypto threat was seen in the Decentralized Autonomous Organization (DAO) hack in 2016. Cyberhackers repeatedly withdrew unauthorised funds and stole 3.6 million Ethereum (ETH), worth $60 million at the time.
Ransomware Attacks
Ransomware attacks occur when a hacker successfully installs malware on a victim’s smart device through malicious emails or infected file downloads. The hacker blocks access and encrypts critical files while demanding a crypto payment for ransom to decrypt the files.
In 2021, the REvil group, a ransomware gang, demanded $70 million in Bitcoin from over 200 firms that were their victim. Subsequently, the US Colonial Pipeline fell victim to another ransomware attacker, DarkSide, and paid a ransom of 75 bitcoins worth $4.4 million at the time.
51% Attacks
In 51% attacks, a malicious group of cybercriminals controls over half of the blockchain’s mining and computational power. This removes the blockchain network’s inherent transparency and decentralisation.
A single entity of crypto hackers with major network control gains the power to block confirmations of new payments while placing priority on their transactions.
They can fraudulently force the double-spending of a crypto coin—creating another transaction with the same crypto asset on the blockchain network before the original transaction is confirmed.
On rare occasions, a 51% attack on a smaller blockchain network allows hackers to reverse transactions made while in control of the network and replace them with preferred details. This rarely occurs because of its extreme cost and difficulty.
In 2018, Bitcoin Gold (BTG) was the target of a 51% attack, and $18 million worth of BTG coins were double-spent on its blockchain network.
Best Practices for Crypto Transaction Security: How Paymento Secures You
With the increasing prevalence of cyber threats in crypto, safeguarding your digital assets cannot be overemphasized. Below are some of the best crypto transaction security practices to ensure your crypto funds remain safe.
Protect Your Private Keys
Use cold wallets like Ledger or Trezor to store your crypto assets offline. This will help reduce exposure to cyber threats, prevent crypto hacks and permanent fund loss. Unlike hot wallets, which are constantly connected to the internet, cold wallets prevent unauthorized access from online hackers.
The Mt. Gox hack could have been avoided if crypto assets were stored in a cold wallet and private keys were kept more safely.
Paymento’s non-custodial payment gateway gives you full control of your private keys, meaning no unauthorized access from intermediaries and individuals with malicious intent.
Use Extended Public Keys (xPub)
An Extended public key is a master public key used to generate mini-public keys (wallet addresses) without revealing your private keys. It is usually called the ‘parent public key’ because it births other derived wallet addresses called ‘children public keys’ that can be used to receive payments.
Paymento supports multiple wallets for xPub key integration, allowing you to create various public keys for transactions. Hence, your private keys are more secure.
End-to-End Data Encryption
End-to-end encryption ensures that your transaction data remains confidential and protected from interception by malicious individuals. This encryption standard guarantees that only the people you give access to can access the encrypted data.
In 2020, Ledger, a crypto wallet provider, was hacked, exposing over 270,000 customers’ emails and phone numbers. Strong data encryption could have prevented this.
When you choose Paymento as your crypto payment gateway, you can worry less about your data privacy. Paymento implements standard data encryption protocols to provide confidentiality and protect your data from malicious attacks.
Two-factor authentication (2FA):
Enabling 2FA on your crypto wallets and exchange accounts adds an extra layer of security to your crypto assets. You reduce the risk of unauthorized access by requiring a secondary authentication method, such as a one-time password (OTP) sent to your mobile device.
In 2021, users of the Liquid crypto exchange lost approximately $90 million after crypto hackers gained unauthorised access to its hot wallets.
Paymento’s strong authentication mechanisms, such as mandatory 2FA for user accounts, prevent this sort of cyber hacking and unauthorised access.
Multi-Signature Wallets:
Multi-signature (multi-sig) wallets require multiple private key approvals before executing a transaction. This feature enhances crypto transaction security, especially for businesses and institutional investors managing large sums of crypto assets.
Bitfinex suffered a hack in 2016, losing $72 million in Bitcoin because it relied on a multi-signature setup with vulnerabilities in its implementation.
Paymento has an adequately implemented multi-signature system with independent key custodians and mandates the approval of all private keys before any transaction is completed. Thereby adding an extra layer of security to your digital assets.
Regular Wallet Updates:
Updating your wallet software and firmware ensures you benefit from the latest security patches and improvements. Cybercriminals often exploit vulnerabilities in outdated software to gain access to funds.
In 2018, a critical vulnerability in the Ethereum Parity wallet permanently froze over $150 million worth of Ether.
Paymento’s regular software updates and security audits prevent these vulnerabilities by detecting lapses early and immediately fixing them before they can be exploited.
Avoid Public WiFi:
Refrain from accessing your crypto wallet on public WiFi networks, as they are susceptible to cyberattacks such as man-in-the-middle (MITM) attacks. If you must access your funds on the go, we recommend you use a virtual private network (VPN) for improved security.
What Does Compliance in Crypto Transactions Mean?
Crypto compliance refers to adhering to regulatory frameworks and legal standards set by governing bodies to ensure secure and lawful transactions. Compliance is crucial for businesses and individuals dealing with digital assets, as failure to comply can lead to penalties or restrictions.
Basic Crypto Compliance Requirements:
- Know Your Customer (KYC): KYC protocols require crypto exchanges and platforms to verify users’ identities through documentation such as government-issued IDs. This helps prevent fraud and money laundering.
- Anti-Money Laundering (AML): AML regulations prevent the illicit use of cryptocurrencies for illegal activities, including terrorism financing and drug trafficking. Crypto platforms must monitor transactions and report suspicious activities to authorities.
- Financial Action Task Force (FATF) Guidelines: The FATF sets global standards for combating financial crimes, including the Travel Rule, which requires crypto exchanges to share transaction details of crypto transfers exceeding a certain threshold.
- General Data Protection Regulation (GDPR): GDPR ensures data privacy and protection for crypto users within the European Union. Exchanges must comply with these regulations to safeguard user data.
Regional Crypto Transaction Regulations:
Crypto regulations vary globally, with different countries enforcing specific legal frameworks:
- United States: The SEC and CFTC oversee crypto regulations, focusing on securities compliance and derivatives trading.
- European Union: The EU implements the MiCA (Markets in Crypto-Assets) regulation to standardize crypto laws.
- China: A ban on crypto payments and mining restricts digital asset activities.
- United Kingdom: The FCA regulates crypto businesses, ensuring consumer protection.
What are the Risks Associated with Crypto Transactions?
Despite the advantages of cryptocurrency, various crypto risks exist that investors and businesses must consider.
- Financial Risks: Market volatility may result in rapid price fluctuations, leading to unexpected financial losses. Fraudulent ICOs and Ponzi schemes trick investors into depositing funds into fake projects.
- Legal Risks: Regulatory uncertainty may lead to sudden policy changes that impact crypto businesses and investments. Non-compliance with AML and KYC laws may result in legal consequences.
- Operational Risks: Loss of private keys results in irreversible loss of funds. Smart contract vulnerabilities can lead to exploits and unauthorized fund withdrawals.
Mitigating Crypto Risks and Preventing Scams
- Conduct thorough research before investing in any cryptocurrency or DeFi project.
- Use decentralised platforms with audited smart contracts to reduce exposure to crypto risks.
- Stay informed about regulatory changes in your region.
- Store private keys securely and use reputable hardware wallets.
- Enable multi-layered security features such as biometric authentication and withdrawal whitelists.
What’s the Future for Crypto Transaction Security?
As blockchain technology advances, more advanced security measures and regulatory frameworks will emerge to improve the safety of crypto transactions. Integrating AI and machine learning will enhance fraud detection, while decentralised identity solutions will provide better crypto compliance mechanisms.
Governments and regulatory bodies will continue refining policies to ensure the responsible adoption of digital assets without stifling innovation.
Final Thoughts
Crypto transactions offer enormous financial freedom and efficiency, but they also come with security challenges and regulatory hurdles. To navigate the digital economy safely, users must implement strong crypto transaction security measures, comply with regulations, and stay informed about potential crypto risks.
Understanding crypto transaction security, compliance, and risks enables you to make informed decisions and protect your digital assets in the evolving blockchain ecosystem.
At Paymento, we understand the importance of secure and compliant crypto transactions. Our platform provides a safe and risk-free gateway for businesses and individuals looking to send, receive, and manage their digital assets effortlessly.
Whether you’re an investor, trader, or business owner, our innovative solutions guarantee fast, secure, and cost-effective transactions. You can boost your revenue, attract global customers, and enjoy instant settlements.
Why wait? Start accepting the most secure crypto payments seamlessly with Paymento today! Your trusted crypto payment gateway with multi-sig wallets, Xpubs, and stablecoin support.
Frequently Asked Questions (FAQs)
Can stolen crypto be recovered?
Due to the irreversible nature of blockchain transactions, recovering stolen funds is challenging. However, authorities and forensic blockchain firms may assist in tracking transactions.
Are all crypto transactions anonymous?
No. Most crypto transactions are pseudonymous, meaning they can be traced through blockchain analysis tools.
How can I ensure my crypto exchange is secure?
Choose crypto exchanges with strong security protocols, multi-signature authentication, and regulatory compliance.
What should I do if I suspect a phishing attack?
Immediately change your passwords, enable 2FA, and report the incident to your exchange or wallet provider.
Are crypto regulations the same in every country?
No, regulations vary by region. Always check your country’s legal framework before engaging in crypto transactions.
What is the safest way to store cryptocurrency?
The safest way to store crypto is by using a hardware (cold) wallet with strong encryption and backup security measures.
What is the best practice for securing private keys?
Store private keys offline, use a hardware wallet, and never share them with anyone.
Can I use my crypto wallet on multiple devices?
Yes, but ensure that all devices are secure and updated with the latest security patches.